Documentation
¶
Documentation
¶
Overview ¶
Package panos interacts with Palo Alto and Panorama devices using the XML API.
Index ¶
- type ARPEntry
- type ARPTable
- type Address
- type AddressGroup
- type AddressGroups
- type AddressObjects
- type Application
- type ApplicationInformation
- type ApplicationReferences
- type AuthMethod
- type CustomURL
- type DeviceGroup
- type DeviceGroups
- type Devices
- type EncryptionProfiles
- type Gateways
- type IKEGateway
- type IKEOptions
- type IKEProfile
- type IPSecProfile
- type InterfaceHardware
- type InterfaceIfnet
- type InterfaceInformation
- type Job
- type Jobs
- type Log
- type LogForwarding
- type LogForwardingMatchList
- type LogForwardingProfile
- type LogParameters
- type Logs
- type NATPolicy
- type NATRule
- type PaloAlto
- func (p *PaloAlto) ARPTable(option ...string) (*ARPTable, error)
- func (p *PaloAlto) AddDevice(serial string, devicegroup ...string) error
- func (p *PaloAlto) AddInterfaceToVirtualRouter(vr, ifname string) error
- func (p *PaloAlto) AddInterfaceToVlan(vlan, ifname string) error
- func (p *PaloAlto) AddInterfaceToZone(name, zonetype, ifname string) error
- func (p *PaloAlto) AddProxyID(tunnel, name, localip, remoteip string) error
- func (p *PaloAlto) AddressGroups(devicegroup ...string) (*AddressGroups, error)
- func (p *PaloAlto) Addresses(devicegroup ...string) (*AddressObjects, error)
- func (p *PaloAlto) ApplicationInfo(name ...string) (*ApplicationInformation, error)
- func (p *PaloAlto) ApplyLogForwardingProfile(logprofile, devicegroup string, rule ...string) error
- func (p *PaloAlto) ApplySecurityProfile(secprofiles *SecurityProfiles, devicegroup string, rule ...string) error
- func (p *PaloAlto) AssignTemplate(name, devices string, stack bool) error
- func (p *PaloAlto) Command(command string) (string, error)
- func (p *PaloAlto) Commit() error
- func (p *PaloAlto) CommitAll(devicegroup string, devices ...string) error
- func (p *PaloAlto) CreateAddress(name, addrtype, address, description string, devicegroup ...string) error
- func (p *PaloAlto) CreateAddressGroup(name, grouptype string, members interface{}, description string, ...) error
- func (p *PaloAlto) CreateDeviceGroup(name, description string, devices []string) error
- func (p *PaloAlto) CreateExternalDynamicList(listtype string, name string, url string, recurrance *Recurrance, ...) error
- func (p *PaloAlto) CreateIKEGateway(name, version, local, peer, psk, mode, profile string, options ...*IKEOptions) error
- func (p *PaloAlto) CreateIKEProfile(name, encryption, authentication, dhgroup string, lifetime string) error
- func (p *PaloAlto) CreateIPSecProfile(name, encryption, authentication, lifetime string, dhgroup ...string) error
- func (p *PaloAlto) CreateIPSecTunnel(name, iface, gateway, profile string) error
- func (p *PaloAlto) CreateInterface(iftype, ifname, comment string, ipaddr ...string) error
- func (p *PaloAlto) CreateLayer3Interface(ifname, ipaddress string, comment ...string) error
- func (p *PaloAlto) CreateObjectsFromCsv(file string) error
- func (p *PaloAlto) CreateRule(name, ruletype string, content *RuleContent, devicegroup ...string) error
- func (p *PaloAlto) CreateService(name, protocol, port, description string, devicegroup ...string) error
- func (p *PaloAlto) CreateServiceGroup(name string, members []string, devicegroup ...string) error
- func (p *PaloAlto) CreateStaticRoute(vr, name, destination, nexthop string, metric ...int) error
- func (p *PaloAlto) CreateTag(name, color, comments string, devicegroup ...string) error
- func (p *PaloAlto) CreateTemplate(name, description string, devices ...string) error
- func (p *PaloAlto) CreateTemplateStack(name, description, templates string, devices ...string) error
- func (p *PaloAlto) CreateURLCategory(name string, urls []string, description string, devicegroup ...string) error
- func (p *PaloAlto) CreateVirtualRouter(name string) error
- func (p *PaloAlto) CreateVlan(name string, vlaninterface ...string) error
- func (p *PaloAlto) CreateVwire(name, interface1, interface2, tagallowed string) error
- func (p *PaloAlto) CreateZone(name, zonetype string, userid bool) error
- func (p *PaloAlto) CryptoProfiles() (*EncryptionProfiles, error)
- func (p *PaloAlto) DeleteAddress(name string, devicegroup ...string) error
- func (p *PaloAlto) DeleteAddressGroup(name string, devicegroup ...string) error
- func (p *PaloAlto) DeleteDeviceGroup(name string) error
- func (p *PaloAlto) DeleteExternalDynamicList(name string, devicegroup ...string) error
- func (p *PaloAlto) DeleteInterface(iftype, ifname string) error
- func (p *PaloAlto) DeleteProxyID(tunnel, name string) error
- func (p *PaloAlto) DeleteService(name string, devicegroup ...string) error
- func (p *PaloAlto) DeleteServiceGroup(name string, devicegroup ...string) error
- func (p *PaloAlto) DeleteStaticRoute(vr, name string) error
- func (p *PaloAlto) DeleteTag(name string, devicegroup ...string) error
- func (p *PaloAlto) DeleteTemplate(name string, stack bool) error
- func (p *PaloAlto) DeleteURLCategory(name string, devicegroup ...string) error
- func (p *PaloAlto) DeleteVirtualRouter(vr string) error
- func (p *PaloAlto) DeleteVlan(vlan string) error
- func (p *PaloAlto) DeleteVwire(name string) error
- func (p *PaloAlto) DeleteZone(name string) error
- func (p *PaloAlto) DeviceGroupNATPolicy(group string) (*NATPolicy, error)
- func (p *PaloAlto) DeviceGroups(devicegroup ...string) (*DeviceGroups, error)
- func (p *PaloAlto) Devices() (*Devices, error)
- func (p *PaloAlto) EditGroup(objecttype, action, object, group string, devicegroup ...string) error
- func (p *PaloAlto) EditURLCategory(action, url, name string, devicegroup ...string) error
- func (p *PaloAlto) IKEGateways() (*Gateways, error)
- func (p *PaloAlto) IPSecTunnels() (*Tunnels, error)
- func (p *PaloAlto) InterfaceInfo() (*InterfaceInformation, error)
- func (p *PaloAlto) Jobs(status interface{}) (*Jobs, error)
- func (p *PaloAlto) LogForwardingProfiles() (*LogForwarding, error)
- func (p *PaloAlto) ModifyGroupsFromCsv(file string) error
- func (p *PaloAlto) NATPolicy() (*NATPolicy, error)
- func (p *PaloAlto) Policy(devicegroup ...string) (*Policy, error)
- func (p *PaloAlto) QueryLogs(logtype string, parameters *LogParameters) (int, error)
- func (p *PaloAlto) RemoveDevice(serial string, devicegroup ...string) error
- func (p *PaloAlto) RemoveInterfaceFromVirtualRouter(vr, ifname string) error
- func (p *PaloAlto) RemoveInterfaceFromVlan(vlan, ifname string) error
- func (p *PaloAlto) RemoveInterfaceFromZone(name, zonetype, ifname string) error
- func (p *PaloAlto) RemoveTagFromObject(tag, object string, devicegroup ...string) error
- func (p *PaloAlto) RemoveTagFromRule(tag, rule string, devicegroup ...string) error
- func (p *PaloAlto) RenameObject(oldname, newname string, devicegroup ...string) error
- func (p *PaloAlto) RestartSystem() error
- func (p *PaloAlto) RetrieveLogs(id int) (*Logs, error)
- func (p *PaloAlto) Routes(vr ...string) (*RoutingTable, error)
- func (p *PaloAlto) SecurityProfileGroups() (*SecurityGroups, error)
- func (p *PaloAlto) ServiceGroups(devicegroup ...string) (*ServiceGroups, error)
- func (p *PaloAlto) Services(devicegroup ...string) (*ServiceObjects, error)
- func (p *PaloAlto) SessionID(id string) (*SessionID, error)
- func (p *PaloAlto) Sessions(filter ...string) (*SessionTable, error)
- func (p *PaloAlto) SetPanoramaServer(primary string, secondary ...string) error
- func (p *PaloAlto) SetShared(shared bool)
- func (p *PaloAlto) TagObject(tag, object string, devicegroup ...string) error
- func (p *PaloAlto) TagRule(tag, rule string, devicegroup ...string) error
- func (p *PaloAlto) Tags(devicegroup ...string) (*Tags, error)
- func (p *PaloAlto) TemplateStacks() (*TemplateStacks, error)
- func (p *PaloAlto) Templates() (*Templates, error)
- func (p *PaloAlto) TestRouteLookup(vr, destination string) (*RouteLookup, error)
- func (p *PaloAlto) TestURL(url string) ([]string, error)
- func (p *PaloAlto) URLCategory(devicegroup ...string) (*URLCategory, error)
- func (p *PaloAlto) XpathClone(xpath, from, newname string) error
- func (p *PaloAlto) XpathConfig(action, xpath string, element ...string) error
- func (p *PaloAlto) XpathGetConfig(configtype, xpath string) (string, error)
- func (p *PaloAlto) XpathMove(xpath, where string, destination ...string) error
- func (p *PaloAlto) XpathMulti(action, xpath, element string) error
- type Policy
- type ProxyID
- type Recurrance
- type Route
- type RouteLookup
- type RoutingTable
- type Rule
- type RuleContent
- type SecurityGroups
- type SecurityProfileGroup
- type SecurityProfiles
- type Serial
- type Service
- type ServiceGroup
- type ServiceGroups
- type ServiceObjects
- type Session
- type SessionID
- type SessionTable
- type SingleSession
- type Tag
- type Tags
- type Template
- type TemplateStack
- type TemplateStacks
- type Templates
- type Tunnel
- type Tunnels
- type URLCategory
- type VsysEntry
Constants ¶
This section is empty.
Variables ¶
This section is empty.
Functions ¶
This section is empty.
Types ¶
type ARPEntry ¶
type ARPEntry struct {
Status string `xml:"status"`
IPAddress string `xml:"ip"`
MACAddress string `xml:"mac"`
TTL string `xml:"ttl"`
Interface string `xml:"interface"`
Port string `xml:"port"`
}
ARPEntry contains information about each individual ARP entry.
type ARPTable ¶
type ARPTable struct {
XMLName xml.Name `xml:"response"`
MaxEntries int `xml:"result>max"`
TotalEntries int `xml:"result>total"`
DefaultTimeout int `xml:"result>timeout"`
Entries []ARPEntry `xml:"result>entries>entry"`
}
ARPTable contains information about all of the ARP entries on the device.
type Address ¶
type Address struct {
Name string `xml:"name,attr"`
IPAddress string `xml:"ip-netmask,omitempty"`
IPRange string `xml:"ip-range,omitempty"`
FQDN string `xml:"fqdn,omitempty"`
Description string `xml:"description,omitempty"`
Tag []string `xml:"tag>member,omitempty"`
}
Address contains information about each individual address object.
type AddressGroup ¶
type AddressGroup struct {
Name string
Type string
Members []string
DynamicFilter string
Description string
Tag []string
}
AddressGroup contains information about each individual address group.
type AddressGroups ¶
type AddressGroups struct {
Groups []AddressGroup
}
AddressGroups contains a slice of all address groups.
type AddressObjects ¶
type AddressObjects struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Addresses []Address `xml:"result>address>entry"`
}
AddressObjects contains a slice of all address objects.
type Application ¶
type Application struct {
ID string `xml:"id,attr"`
Name string `xml:"name,attr"`
OriginCountry string `xml:"ori_country,attr"`
OriginLanguage string `xml:"ori_language,attr"`
Category string `xml:"category"`
Subcategory string `xml:"subcategory"`
Technology string `xml:"technology"`
VirusIdent string `xml:"virus-ident"`
FileTypeIdent string `xml:"file-type-ident"`
TunnelOtherApplications string `xml:"tunnel-other-applications"`
DataIdent string `xml:"data-ident"`
FileForward string `xml:"file-forward"`
IsSAAS string `xml:"is-saas"`
EvasiveBehavior string `xml:"evasive-behavior"`
ConsumeBigBandwidth string `xml:"consume-big-bandwidth"`
UsedByMalware string `xml:"used-by-malware"`
AbleToTransferFile string `xml:"able-to-transfer-file"`
HasKnownVulnerability string `xml:"has-known-vulnerability"`
ProneToMisuse string `xml:"prone-to-misuse"`
PervasiveUse string `xml:"pervasive-use"`
References []ApplicationReferences `xml:"references>entry"`
DefaultPort []string `xml:"default>port>member"`
UseApplications []string `xml:"use-applications>member"`
ImplicitUseApplications []string `xml:"implicit-use-applications>member"`
Risk int `xml:"risk"`
}
Application contains information about each individual application.
type ApplicationInformation ¶
type ApplicationInformation struct {
Applications []Application
}
ApplicationInformation contains information about every application.
type ApplicationReferences ¶
ApplicationReferences contains the name and link of the reference site.
type AuthMethod ¶
AuthMethod defines how we want to authenticate to the device. If using a username and password to authenticate, the Credentials field must contain the username and password , respectively (e.g. []string{"admin", "password"}). If you are using the API key for authentication, provide the entire key for the APIKey field.
type CustomURL ¶
type CustomURL struct {
Name string `xml:"name,attr"`
Description string `xml:"description,omitempty"`
Members []string `xml:"list>member,omitempty"`
}
CustomURL contains information about each individual custom URL category object.
type DeviceGroup ¶
DeviceGroup contains information about each individual device-group.
type DeviceGroups ¶
type DeviceGroups struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
DeviceGroup []DeviceGroup `xml:"result>devicegroups>entry"`
}
DeviceGroups lists all of the device-group's in Panorama.
type Devices ¶
type Devices struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Devices []Serial `xml:"result>devices>entry"`
}
Devices lists all of the devices in Panorama.
type EncryptionProfiles ¶
type EncryptionProfiles struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
IKE []IKEProfile
IPSec []IPSecProfile
}
EncryptionProfiles contains information about all of the IKE and IPSec crypto profiles on a device.
type Gateways ¶
type Gateways struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Gateways []IKEGateway `xml:"result>gateway>entry"`
}
Gateways contains information of all the IKE gateways configured on a device.
type IKEGateway ¶
type IKEGateway struct {
Name string `xml:"name,attr"`
PSK string `xml:"authentication>pre-shared-key>key"`
Version string `xml:"protocol>version"`
V1DeadPeerDetection string `xml:"protocol>ikev1>dpd>enable"`
V1ExchangeMode string `xml:"protocol>ikev1>exchange-mode"`
V2DeadPeerDetection string `xml:"protocol>ikev2>dpd>enable"`
V2CookieValidation string `xml:"protocol>ikev2>require-cookie"`
LocalAddress string `xml:"local-address>ip"`
LocalInterface string `xml:"local-address>interface"`
PeerAddress string `xml:"peer-address>ip"`
PeerDynamicAddress string `xml:"peer-address>dynamic"`
LocalID string `xml:"local-id>id"`
LocalIDType string `xml:"local-id>type"`
PeerID string `xml:"peer-id>id"`
PeerIDType string `xml:"peer-id>type"`
NATTraversal string `xml:"protocol-common>nat-traversal>enable"`
Fragmentation string `xml:"protocol-common>fragmentation>enable"`
PassiveMode string `xml:"protocol-common>passive-mode"`
}
IKEGateway contains information about each individual IKE gateway.
type IKEOptions ¶
type IKEOptions struct {
// PassiveMode decides whether or not to have the firewall only respond to IKE connections
// and never initiate them.
PassiveMode bool
// NATTraversal enables UDP encapsulation to be used on IKE and UDP protocols, enabling them
// to pass through intermediate NAT devices. Enable NAT Traversal if Network Address Translation (NAT)
// is configured on a device between the IPSec VPN terminating points.
NATTraversal bool
// LocalIDType must be one of: ipaddr, fqdn, ufqdn or keyid
LocalIDType string
// LocalID specifies either the IP address, FQDN, email address, or binary format
// ID string in HEX.
LocalID string
// PeerIDType must be one of: ipaddr, fqdn, ufqdn or keyid
PeerIDType string
// PeerID specifies either the IP address, FQDN, email address, or binary format
// ID string in HEX.
PeerID string
// DPDRetry defines the delay before retrying. The value must be between 2 and 100.
DPDRetry int
// DPDInterval defines the interval between tries. The value must be between 2 and 100.
DPDInterval int
// RequireCookie enables Strict Cookie Validation on the IKE gateway.
RequireCookie bool
}
IKEOptions ...
type IKEProfile ¶
type IKEProfile struct {
Name string `xml:"name,attr"`
Encryption []string `xml:"encryption>member"`
Authentication []string `xml:"hash>member"`
DHGroup []string `xml:"dh-group>member"`
LifetimeHours int `xml:"lifetime>hours"`
LifetimeSeconds int64 `xml:"lifetime>seconds"`
LifetimeDays int `xml:"lifetime>days"`
LifetimeMinutes int64 `xml:"lifetime>minutes"`
}
IKEProfile contains information about each individual IKE crypto profile.
type IPSecProfile ¶
type IPSecProfile struct {
Name string `xml:"name,attr"`
ESPEncryption []string `xml:"esp>encryption>member"`
ESPAuthentication []string `xml:"esp>authentication>member"`
AHAuthentication []string `xml:"ah>authentication>member"`
DHGroup string `xml:"dh-group"`
LifetimeHours int `xml:"lifetime>hours"`
LifetimeSeconds int64 `xml:"lifetime>seconds"`
LifetimeDays int `xml:"lifetime>days"`
LifetimeMinutes int64 `xml:"lifetime>minutes"`
}
IPSecProfile contains information about each individual IPSec crypto profile.
type InterfaceHardware ¶
type InterfaceHardware struct {
Name string `xml:"name"`
Duplex string `xml:"duplex"`
Type string `xml:"type"`
State string `xml:"state"`
AEMember []string `xml:"ae_member>member"`
Settings string `xml:"st"`
MACAddress string `xml:"mac"`
Mode string `xml:"mode"`
Speed string `xml:"speed"`
ID int `xml:"id"`
}
InterfaceHardware contains all of the physical interface information, such as MAC address, duplex.
type InterfaceIfnet ¶
type InterfaceIfnet struct {
Name string `xml:"name"`
Zone string `xml:"zone"`
VirtualRouter string `xml:"fwd"`
Vsys int `xml:"vsys"`
DynamicAddress string `xml:"dyn-addr"`
IPv6Addres string `xml:"addr6"`
Tag int `xml:"tag"`
IPAddress string `xml:"ip"`
ID int `xml:"id"`
Address string `xml:"addr"`
}
InterfaceIfnet contains all of the logical interface information, such as IP address and zone.
type InterfaceInformation ¶
type InterfaceInformation struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Logical []InterfaceIfnet `xml:"result>ifnet>entry"`
Hardware []InterfaceHardware `xml:"result>hw>entry"`
}
InterfaceInformation contains all of the logical and physical interface information.
type Job ¶
type Job struct {
ID int `xml:"id"`
User string `xml:"user"`
Type string `xml:"type"`
Status string `xml:"status"`
Queued string `xml:"queued"`
Stoppable string `xml:"stoppable"`
Result string `xml:"result"`
Description string `xml:"description,omitempty"`
QueuePosition int `xml:"positionInQ"`
Progress string `xml:"progress"`
Details []string `xml:"details>line"`
Warnings string `xml:"warnings,omitempty"`
StartTime string `xml:"tdeq"`
EndTime string `xml:"tfin"`
}
Job holds information about each individual job.
type Jobs ¶
type Jobs struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Jobs []Job `xml:"result>job"`
}
Jobs holds information about all jobs on the device.
type Log ¶
type Log struct {
DeviceName string `xml:"device_name,omitempty"`
Serial string `xml:"serial,omitempty"`
Rule string `xml:"rule,omitempty"`
TimeGenerated string `xml:"time_generated,omitempty"`
TimeReceived string `xml:"time_received,omitempty"`
Type string `xml:"type,omitempty"`
Subtype string `xml:"subtype,omitempty"`
From string `xml:"from,omitempty"`
To string `xml:"to,omitempty"`
Source string `xml:"src,omitempty"`
SourceUser string `xml:"srcuser,omitempty"`
SourcePort int `xml:"sport,omitempty"`
SourceCountry string `xml:"srcloc,omitempty"`
Destination string `xml:"dst,omitempty"`
DestinationPort int `xml:"dport,omitempty"`
DestinationCountry string `xml:"dstloc,omitempty"`
Application string `xml:"app,omitempty"`
Action string `xml:"action,omitempty"`
NATSourceIP string `xml:"natsrc,omitempty"`
NATSourcePort int `xml:"natsport,omitempty"`
NATDestinationIP string `xml:"natdst,omitempty"`
NATDestinationPort int `xml:"natdport,omitempty"`
Packets int `xml:"packets,omitempty"`
PacketsSent int `xml:"pkts_sent,omitempty"`
PacketsReceived int `xml:"pkts_received,omitempty"`
Bytes int `xml:"bytes,omitempty"`
BytesSent int `xml:"bytes_sent,omitempty"`
BytesReceived int `xml:"bytes_received,omitempty"`
SessionID int `xml:"sessionid,omitempty"`
SessionEndReason string `xml:"session_end_reason,omitempty"`
RepeatCount int `xml:"repeatcnt,omitempty"`
Start string `xml:"start,omitempty"`
Elapsed string `xml:"elapsed,omitempty"`
Category string `xml:"category,omitempty"`
ThreatCategory string `xml:"thr_category,omitempty"`
ThreatName string `xml:"threatid,omitempty"`
ThreatID int `xml:"tid,omitempty"`
Misc string `xml:"misc,omitempty"`
Severity string `xml:"severity,omitempty"`
Direction string `xml:"direction,omitempty"`
InboundInterface string `xml:"inbound_if,omitempty"`
OutboundInterface string `xml:"outbound_if,omitempty"`
ID int `xml:"logid,attr"`
Domain int `xml:"domain,omitempty"`
ReceiveTime string `xml:"receive_time,omitempty"`
SequenceNumber string `xml:"seqno,omitempty"`
ActionFlags string `xml:"actionflags,omitempty"`
ConfigVersion int `xml:"config_ver,omitempty"`
Vsys string `xml:"vsys,omitempty"`
Logset string `xml:"logset,omitempty"`
Flags string `xml:"flags,omitempty"`
Pcap string `xml:"flag-pcap,omitempty"`
PcapID int `xml:"pcap_id,omitempty"`
Flagged string `xml:"flag-flagged,omitempty"`
Proxy string `xml:"flag-proxy,omitempty"`
URLDenied string `xml:"flag-url-denied,omitempty"`
NAT string `xml:"flag-nat,omitempty"`
CaptivePortal string `xml:"captive-portal"`
NonStandardDestinationPort string `xml:"non-std-dport"`
Transaction string `xml:"transaction,omitempty"`
PBFClient2Server string `xml:"pbf-c2s,omitempty"`
PBFServer2Client string `xml:"pbf-s2c,omitempty"`
TemporaryMatch string `xml:"temporary-match,omitempty"`
SymmetricReturn string `xml:"sym-return,omitempty"`
SSLDecryptMirror string `xml:"decrypt-mirror,omitempty"`
CredentialDetected string `xml:"credential-detected,omitempty"`
MPTCP string `xml:"flag-mptcp-set,omitempty"`
TunnelInspected string `xml:"flag-tunnel-inspected,omitempty"`
ReconExcluded string `xml:"flag-recon-excluded,omitempty"`
Protocol string `xml:"proto,omitempty"`
TunnelType string `xml:"tunnel,omitempty"`
TPadding int `xml:"tpadding,omitempty"`
CPadding int `xml:"cpadding,omitempty"`
TunnelIMSI int `xml:"tunnelid_imsi,omitempty"`
VsysID int `xml:"vsys_id,omitempty"`
ParentSessionID int `xml:"parent_session_id,omitempty"`
ReportID int `xml:"reportid,omitempty"`
URLIndex int `xml:"url_idx,omitempty"`
HTTPMethod string `xml:"http_method,omitempty"`
XForwardedFor string `xml:"xff,omitempty"`
Referer string `xml:"referer,omitempty"`
UserAgent string `xml:"user_agent,omitempty"`
SignatureFlags string `xml:"sig_flags,omitempty"`
ContentVersion string `xml:"contentver,omitempty"`
FileDigest string `xml:"filedigest,omitempty"`
Filetype string `xml:"filetype,omitempty"`
Sender string `xml:"sender,omitempty"`
Recipient string `xml:"recipient,omitempty"`
Subject string `xml:"subject,omitempty"`
Cloud string `xml:"cloud,omitempty"`
Padding int `xml:"padding,omitempty"`
ActionSource string `xml:"action_source,omitempty"`
TunnelID int `xml:"tunnelid,omitempty"`
IMSI string `xml:"imsi,omitempty"`
MonitorTag string `xml:"monitortag,omitempty"`
IMEI string `xml:"imei,omitempty"`
DeviceGroupHierarchy1 int `xml:"dg_hier_level_1,omitempty"`
DeviceGroupHierarchy2 int `xml:"dg_hier_level_2,omitempty"`
DeviceGroupHierarchy3 int `xml:"dg_hier_level_3,omitempty"`
DeviceGroupHierarchy4 int `xml:"dg_hier_level_4,omitempty"`
Host string `xml:"host,omitempty"`
Command string `xml:"cmd,omitempty"`
Admin string `xml:"admin,omitempty"`
Client string `xml:"client,omitempty"`
Result string `xml:"result,omitempty"`
Path string `xml:"path,omitempty"`
BeforeChangePreview string `xml:"before-change-preview,omitempty"`
AfterChangePreview string `xml:"after-change-preview,omitempty"`
FullPath string `xml:"full-path,omitempty"`
EventID string `xml:"eventid,omitempty"`
Module string `xml:"module,omitempty"`
Description string `xml:"opaque,omitempty"`
}
Log holds information about each individual log retrieved for the following log-types:
config, system, traffic, threat, wildfire, url, data
Certain fields are omitted or populated based on the log type that is specified when querying the system. See https://goo.gl/PPLjVZ for the fields assigned for the different log types.
type LogForwarding ¶
type LogForwarding struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Profiles []LogForwardingProfile `xml:"result>profiles>entry"`
}
LogForwarding contains a list of all log forwarding profiles on the device.
type LogForwardingMatchList ¶
type LogForwardingMatchList struct {
Name string `xml:"name,attr"`
SendToPanorama string `xml:"send-to-panorama"`
LogType string `xml:"log-type"`
Filter string `xml:"filter"`
}
LogForwardingMatchList contains all of the match criteria in a log forwarding profile.
type LogForwardingProfile ¶
type LogForwardingProfile struct {
Name string `xml:"name,attr"`
MatchList []LogForwardingMatchList `xml:"match-list>entry"`
}
LogForwardingProfile contains information about each individual log forwarding profile.
type LogParameters ¶
type LogParameters struct {
// Query specifies the match criteria for the logs. This is similar to the query provided in the web interface under the Monitor
// tab when viewing the logs. The query must be URL encoded.
Query string
// NLogs specifies the number of logs to retrieve. The default is 20 when the parameter is not specified. The maximum is 5000.
NLogs int
// Skip specifies the number of logs to skip when doing a log retrieval. The default is 0. This is useful when retrieving
// logs in batches where you can skip the previously retrieved logs.
Skip int
// Direction specifies whether logs are shown oldest first (forward) or newest first (backward). Default is backward.
Direction string
// Action is not used at the moment. Log data sizes can be large so the API uses an asynchronous job scheduling approach to retrieve
// log data. The initial query returns a Job ID (job-id) that you can then use for future queries with the action parameter: action=get
// will check status of an active job or retrieve the log data when the status is FIN (finished).
Action string
}
LogParameters specifies additional parameters that can be used when retrieving logs. These are all optional.
type Logs ¶
type Logs struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
StartTime string `xml:"result>job>tdeq"`
EndTime string `xml:"result>job>tfin"`
JobStatus string `xml:"result>job>status"`
JobID int `xml:"result>job>id"`
Logs []Log `xml:"result>log>logs>entry"`
}
Logs holds all of the log data retrieved from querying the system.
type NATPolicy ¶
type NATPolicy struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Rules []NATRule `xml:"result>rules>entry"`
}
NATPolicy contains information about all of the NAT rules on the device.
type NATRule ¶
type NATRule struct {
Name string `xml:"name,attr"`
From []string `xml:"from>member"`
To []string `xml:"to>member"`
Source []string `xml:"source>member"`
Destination []string `xml:"destination>member"`
Service []string `xml:"service>member"`
SrcDynamicInterfaceIP string `xml:"source-translation>dynamic-ip-and-port>interface-address>ip"`
SrcDynamicInterface string `xml:"source-translation>dynamic-ip-and-port>interface-address>interface"`
SrcDynamicIPAndPortTranslatedIP string `xml:"source-translation>dynamic-ip-and-port>translated-address>member"`
SrcDynamicTranslatedIP []string `xml:"source-translation>dynamic-ip>translated-address>member"`
DestinationTransltedIP string `xml:"destination-translation>translated-address"`
SrcStaticTranslatedIP string `xml:"source-translation>static-ip>translated-address"`
BiDirectional string `xml:"source-translation>static-ip>bi-directional"`
}
NATRule contains information about each individual NAT rule.
type PaloAlto ¶
type PaloAlto struct {
Host string
Key string
URI string
Platform string
Model string
Serial string
SoftwareVersion string
DeviceType string
Panorama bool
IPAddress string
Netmask string
DefaultGateway string
MACAddress string
Time string
Uptime string
GPClientPackageVersion string
GPDatafileVersion string
GPDatafileReleaseDate string
GPClientlessVPNVersion string
GPClientlessVPNReleaseDate string
AppVersion string
AppReleaseDate string
AntiVirusVersion string
AntiVirusReleaseDate string
ThreatVersion string
ThreatReleaseDate string
WildfireVersion string
WildfireReleaseDate string
URLDB string
URLFilteringVersion string
LogDBVersion string
MultiVsys string
OperationalMode string
}
PaloAlto is a container for our session state. It also holds information about the device that is gathered upon a successful connection to it.
func NewSession ¶
func NewSession(host string, authmethod *AuthMethod) (*PaloAlto, error)
NewSession sets up our connection to the Palo Alto firewall or Panorama device. The authmethod parameter is used to define two ways of authenticating to the device. One is via username/password, the other is with the API key if you already have generated it. Please see the documentation for the AuthMethod struct for further details.
func (*PaloAlto) ARPTable ¶
ARPTable will gather all of the ARP entires on the device. Without any parameters, it will return all ARP entries. You can specify an interface name for the option parameter if you choose to only view the ARP entries for that specific interface (e.g. "ethernet1/1.200" or "ethernet1/21"). Status codes are as follows:
s - static, c - complete, e - expiring, i - incomplete.
func (*PaloAlto) AddDevice ¶
AddDevice will add a new device to a Panorama. If you specify the optional devicegroup parameter, it will also add the device to the given device-group.
func (*PaloAlto) AddInterfaceToVirtualRouter ¶
AddInterfaceToVirtualRouter will add an interface or interfaces to the given virtual-router. Separate multiple interfaces using a comma (e.g. "ethernet1/2, ethernet1/3").
func (*PaloAlto) AddInterfaceToVlan ¶
AddInterfaceToVlan will add an interface or interfaces to the given vlan. Separate multiple interfaces using a comma (e.g. "ethernet1/2, ethernet1/3").
func (*PaloAlto) AddInterfaceToZone ¶
AddInterfaceToZone adds an interface or interfaces to the given zone. Zonetype must be one of tap, vwire, layer2, layer3. Separate multiple interfaces using a comma (e.g. "ethernet1/2, ethernet1/3").
func (*PaloAlto) AddProxyID ¶
AddProxyID will add a new proxy-id to the given IPsec tunnel.
func (*PaloAlto) AddressGroups ¶
func (p *PaloAlto) AddressGroups(devicegroup ...string) (*AddressGroups, error)
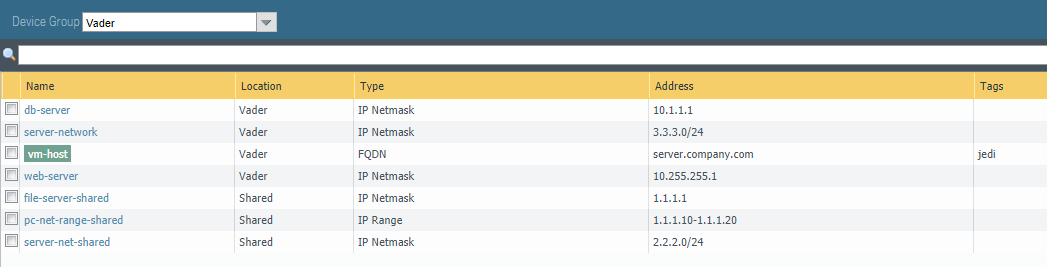
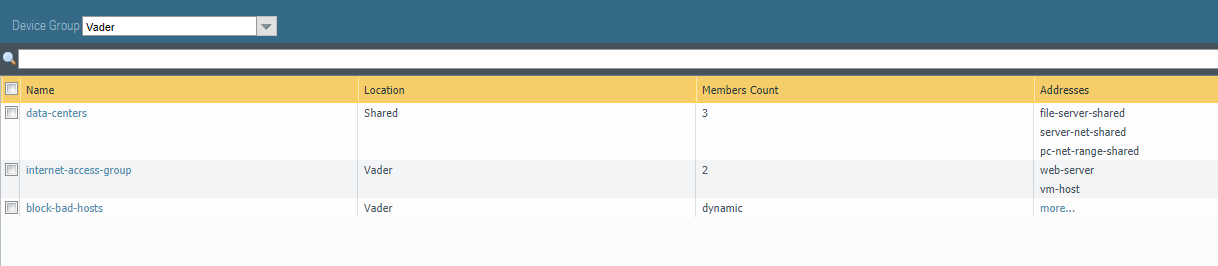
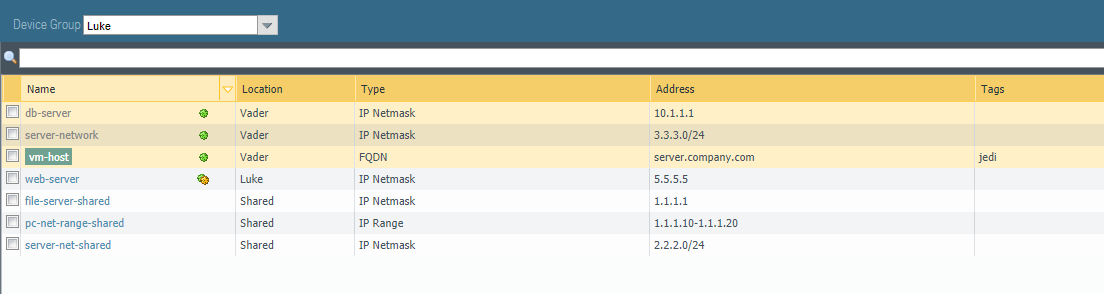
AddressGroups returns information about all of the address groups. You can (optionally) specify a device-group when ran against a Panorama device. If no device-group is specified, then all address groups are returned, including shared objects if run against a Panorama device.
func (*PaloAlto) Addresses ¶
func (p *PaloAlto) Addresses(devicegroup ...string) (*AddressObjects, error)
Addresses returns information about all of the address objects. You can (optionally) specify a device-group when ran against a Panorama device. If no device-group is specified, then all objects are returned, including shared objects if run against a Panorama device.
func (*PaloAlto) ApplicationInfo ¶
func (p *PaloAlto) ApplicationInfo(name ...string) (*ApplicationInformation, error)
ApplicationInfo gathers information about every pre-defined application on the device.
func (*PaloAlto) ApplyLogForwardingProfile ¶
ApplyLogForwardingProfile will apply a Log Forwarding profile to every rule in the policy for the given device-group. If you wish to apply it to a single rule, instead of every rule in the policy, you can (optionally) specify the rule name as the last parameter. For policies with a large number of rules, this process may take a few minutes to complete.
func (*PaloAlto) ApplySecurityProfile ¶
func (p *PaloAlto) ApplySecurityProfile(secprofiles *SecurityProfiles, devicegroup string, rule ...string) error
ApplySecurityProfile will apply the following security profiles to every rule in teh policy for the given device-group:
URL Filtering, File-Blocking, Antivirus, Anti-Spyware, Vulnerability, Wildfire ¶
If you wish to apply it to a single rule, instead of every rule in the policy, you can (optionally) specify the rule name as the last parameter. You can also specify a security group profile instead of individual profiles. This is done by ONLY populating the Group field in the SecurityProfiles struct. For policies with a large number of rules, this process may take a few minutes to complete.
func (*PaloAlto) AssignTemplate ¶
AssignTemplate will assign devices to the given template. Devices must be serial numbers, and each serial must be separated by a comma (e.g. "010101010101, 020202020202"). If you are assigning devices to a template stack, then specify "true" for the stack parameter, otherwise specifying "false" will only assign devices to a single template. Template stacks are ONLY available on Panorama version 7.0.0 and higher.
func (*PaloAlto) Command ¶
Command lets you run any operational mode command against the given device, and it returns the output. You must use the XML-formatted version of the command string as if you were calling the API yourself, (e.g. "<show><running><ippool></ippool></running></show>")
func (*PaloAlto) Commit ¶
Commit issues a commit on the device. When issuing a commit against a Panorama device, the configuration will only be committed to Panorama, and not an individual device-group.
func (*PaloAlto) CommitAll ¶
CommitAll issues a commit to a Panorama device, for the given devicegroup. If you wish to push to specific firewalls within the specified device group only, add each firewalls serial number as an additional parameter, (e.g. CommitAll("Some-DeviceGroup", "000000000001", "000000000002")).
func (*PaloAlto) CreateAddress ¶
func (p *PaloAlto) CreateAddress(name, addrtype, address, description string, devicegroup ...string) error
CreateAddress will add a new address object to the device. Addrtype should be one of ip, range, or fqdn. If creating an address object on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) CreateAddressGroup ¶
func (p *PaloAlto) CreateAddressGroup(name, grouptype string, members interface{}, description string, devicegroup ...string) error
CreateAddressGroup will create a new static or dynamic address group on the device, as specified by the grouptype parameter. If you are creating a static address group, you must add pre-existing members to the group by specifying them using a []string type, for the members parameter. You can specify this as a variable like so:
hosts := []string{"web-server", "db-server", "mail-server"}
When creating a dynamic address group, the match criteria (tags) must be a string type, specified for the members parameter like so:
match := "'web-servers' and 'dmz-servers'"
If you do not want to include a description, just leave the parameter blank using double-quotes (""). If creating an address group on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) CreateDeviceGroup ¶
CreateDeviceGroup will create a new device-group on a Panorama device. You can add devices as well by specifying the serial numbers in a string slice ([]string). Specify "nil" if you do not wish to add any.
func (*PaloAlto) CreateExternalDynamicList ¶
func (p *PaloAlto) CreateExternalDynamicList(listtype string, name string, url string, recurrance *Recurrance, devicegroup ...string) error
CreateExternalDynamicList will create an external dynamic list on the device. Listtype must be one of:
ip, domain, or url
Configuring the recurrance requires you to use the `Recurrance` struct when passing the configuration for this parameter - please see the documentation for that struct. If creating an EDL on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) CreateIKEGateway ¶
func (p *PaloAlto) CreateIKEGateway(name, version, local, peer, psk, mode, profile string, options ...*IKEOptions) error
CreateIKEGateway creates a new IKE gateway on the device. For the IKE version parameter, you must specify one of the following: v1, v2, or v2-preferred. The local parameter specifies the local interface and IP address to use. If you do not need an IP address, just specify the interface name (e.g. "ethernet1/1"). If you do have an IP address assigned, then you must enclose the interface name and IP address within quotes, separated by a space in between (e.g. "ethernet1/1 10.1.1.1/24"). The peer must be an IP address or the word "dynamic." Mode must be one of 'auto', 'main', or 'aggressive.' Profile is the name of a pre-existing IKE crypto profile on the device. The options parameter is optional, and contains additional IKE parameters that you can set. Please see the documentation for the IKEOptions struct.
func (*PaloAlto) CreateIKEProfile ¶
func (p *PaloAlto) CreateIKEProfile(name, encryption, authentication, dhgroup string, lifetime string) error
CreateIKEProfile creates a new IKE crypto profile on the device. Please see the below options that each parameter must contain at least one of (you can have multiple).
Encryption: des, 3des, aes-128-cbc, aes-192-cbc, aes-256-cbc
Authentication: md5, sha1, sha256, sha384, sha512
Diffe-Hellman Group: 1, 2, 5, 14, 19, 20
For lifetime, you must specify the value, followed by seconds, minutes, hours, or days, all surrounded in quotes (e.g. "8 hours" or "86400 seconds").
func (*PaloAlto) CreateIPSecProfile ¶
func (p *PaloAlto) CreateIPSecProfile(name, encryption, authentication, lifetime string, dhgroup ...string) error
CreateIPSecProfile creates a new IPSec crypto profile on the device. Please see the below options that each parameter must contain at least one of (you can have multiple).
Encryption: des, 3des, aes-128-cbc, aes-192-cbc, aes-256-cbc, aes-128-ccm, aes-192-gcm, aes-256-gcm
Authentication: md5, sha1, sha256, sha384, sha512
Diffe-Hellman Group: 1, 2, 5, 14, 19, 20
For lifetime, you must specify the value, followed by seconds, minutes, hours, or days, all surrounded in quotes (e.g. "8 hours" or "86400 seconds").
func (*PaloAlto) CreateIPSecTunnel ¶
CreateIPSecTunnel creates a new IPSec tunnel on the device. The iface parameter must be the name of a tunnel interface (e.g. "tunnel.1"). The gateway and profile settings must contain the name of a pre-existing IKE gateway and IPSec crypto profile, respectively.
func (*PaloAlto) CreateInterface ¶
CreateInterface creates the given interface type specified in the `iftype“ parameter (e.g. tap, vwire, layer2, layer3, vlan, loopback or tunnel). If adding a sub-interface, be sure to append the VLAN tag to the interface name (e.g. ethernet1/1.700). The (optional) ipaddr parameter allows you to assign an IP address to a layer 3/vlan/loopback or tunnel interface, or an IP classifier to a virtual-wire sub-interface. You do not need to specify the ipaddr parameter on a tap or layer2 interface type. Note that you must specify the subnet mask in CIDR notation when including an IP address.
func (*PaloAlto) CreateLayer3Interface ¶
CreateLayer3Interface adds a new layer-3 interface or sub-interface to the device. If adding a sub-interface, be sure to append the VLAN tag to the interface name (e.g. ethernet1/1.700). You must also specify the subnet mask in CIDR notation when specifying the IP address.
func (*PaloAlto) CreateObjectsFromCsv ¶
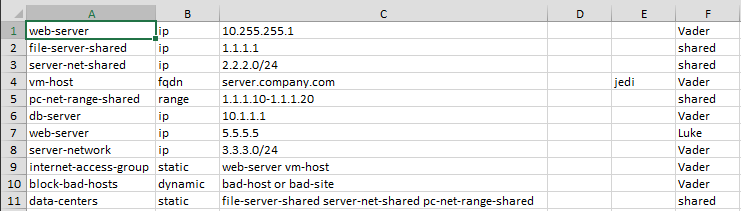
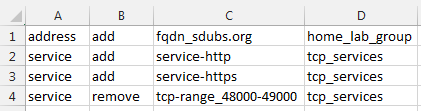
CreateObjectsFromCsv takes a CSV file and creates the given address or service objects, and address or service groups defined within. The format of the CSV file must follow this layout:
name,type,value,description (optional),tag (optional),device-group
See https://github.com/scottdware/go-panos#creating-objects-from-a-csv-file for complete documentation and examples.
func (*PaloAlto) CreateRule ¶
func (p *PaloAlto) CreateRule(name, ruletype string, content *RuleContent, devicegroup ...string) error
CreateRule will create a new rule on the device. If you are connected to a Panorama device, then you must specify the device-group as the last parameter. You do not need this when connected to a firewall.
Ruletype must be one of:
pre, post, local (only if used on a firewall)
You will need to create the rules contents within the RuleContent struct. Please see the documentation for the struct on how to structure it.
func (*PaloAlto) CreateService ¶
func (p *PaloAlto) CreateService(name, protocol, port, description string, devicegroup ...string) error
CreateService adds a new service object to the device. Port can be a single port number, range (1-65535), or comma separated (80, 8080, 443). If creating a service on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) CreateServiceGroup ¶
CreateServiceGroup will create a new service group on the device. You can specify members to add by using a []string variable (e.g. members := []string{"tcp-service1", "udp-service1"}). If creating a service group on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) CreateStaticRoute ¶
CreateStaticRoute adds a new static route to a given virtual-router. For the destination, you must include the mask (e.g. "192.168.0.0/24" or "0.0.0.0/0"). For nexthop, you can also specify an interface instead of an IP address. You can optionally specify a metric for the route (default metric is 10).
func (*PaloAlto) CreateTag ¶
CreateTag will add a new tag to the device. You can use the following colors:
Red, Green, Blue, Yellow, Copper, Orange, Purple, Gray, Light Green, Cyan, Light Gray, Blue Gray, Lime, Black, Gold, Brown.
If creating a tag on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) CreateTemplate ¶
CreateTemplate adds a new template to Panorama. If you wish to associate devices, then separate their serial numbers with a comma (e.g. "0101010101, 0202020202").
func (*PaloAlto) CreateTemplateStack ¶
func (p *PaloAlto) CreateTemplateStack(name, description, templates string, devices ...string) error
CreateTemplateStack adds a new template stack to Panorama. If you are assigning multiple templates to the stack, the values for the templates parameter must be separated by a comma (e.g. "user_template, object_template"). If you wish to associate devices, then separate their serial numbers with a comma, just like you would template names. This is ONLY available on Panorama version 7.0.0 and higher.
func (*PaloAlto) CreateURLCategory ¶
func (p *PaloAlto) CreateURLCategory(name string, urls []string, description string, devicegroup ...string) error
CreateURLCategory creates a custom URL category to be used in a policy. When specifying multiple URL's, use a []string variable for the url parameter (e.g. members := []string{"www.*.com", "*.somesite.net"}). If creating a URL category on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) CreateVirtualRouter ¶
CreateVirtualRouter will add a new virtual-router to the device.
func (*PaloAlto) CreateVlan ¶
CreateVlan will add a new layer 2 vlan to the device. Optionally, if you wish to assign a vlan interface to the vlan, specify the interface name as the last parameter. Otherwise, only specify the name of the vlan when creating it.
func (*PaloAlto) CreateVwire ¶
CreateVwire creates a virtual-wire on the device. For the tagallowed parameter, enter integers (e.g. 10) or ranges (100-200) separated by commas (e.g. 1-10,15,20-30). Integer values can be between 0 and 4094.
func (*PaloAlto) CreateZone ¶
CreateZone will add a new zone to the device. Zonetype must be one of tap, vwire, layer2, layer3. If you wish to enable user-id on the zone, specify true for the userid parameter, false if not.
func (*PaloAlto) CryptoProfiles ¶
func (p *PaloAlto) CryptoProfiles() (*EncryptionProfiles, error)
CryptoProfiles will return a list of all configured IKE and IPSec crypto profiles on the device.
func (*PaloAlto) DeleteAddress ¶
DeleteAddress will remove an address object from the device. If deleting an address object on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) DeleteAddressGroup ¶
DeleteAddressGroup will remove an address group from the device. If deleting an address group on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) DeleteDeviceGroup ¶
DeleteDeviceGroup will delete the given device-group from Panorama.
func (*PaloAlto) DeleteExternalDynamicList ¶
DeleteExternalDynamicList removes an external dynamic list from the device. If deleting an EDL on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) DeleteInterface ¶
DeleteInterface removes an interface or sub-interface from the device. You must specify the interface type in the iftype parameter (e.g. tap, vwire, layer2, layer3, vlan, loopback or tunnel).
func (*PaloAlto) DeleteProxyID ¶
DeleteProxyID will remove a proxy-id from the given IPsec tunnel.
func (*PaloAlto) DeleteService ¶
DeleteService will remove a service object from the device. If deleting a service on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) DeleteServiceGroup ¶
DeleteServiceGroup will remove a service group from the device. If deleting a service group on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) DeleteStaticRoute ¶
DeleteStaticRoute will remove a static route from the device.
func (*PaloAlto) DeleteTag ¶
DeleteTag will remove a tag from the device. If deleting a tag on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) DeleteTemplate ¶
DeleteTemplate removes the given template from Panorama. If you wish to delete a template stack, then specify "true" for the stack parameter, otherwise specifying "false" will only delete single templates. Template stacks are ONLY available on Panorama version 7.0.0 and higher.
func (*PaloAlto) DeleteURLCategory ¶
DeleteURLCategory removes a custom URL category from the device. If deleting a URL category on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) DeleteVirtualRouter ¶
DeleteVirtualRouter removes a virtual-router from the device.
func (*PaloAlto) DeleteVlan ¶
DeleteVlan removes a vlan from the device.
func (*PaloAlto) DeleteVwire ¶
DeleteVwire removes a virtual-wire from the device.
func (*PaloAlto) DeleteZone ¶
DeleteZone will remove a zone from the device.
func (*PaloAlto) DeviceGroupNATPolicy ¶
DeviceGroupNATPolicy returns information about the NAT policy on a given device group.
func (*PaloAlto) DeviceGroups ¶
func (p *PaloAlto) DeviceGroups(devicegroup ...string) (*DeviceGroups, error)
DeviceGroups returns information about all of the device-groups in Panorama, and what devices are linked to them, along with detailed information about each device. You can (optionally) specify a specific device-group if you wish.
func (*PaloAlto) Devices ¶
Devices returns information about all of the devices that are managed by Panorama.
func (*PaloAlto) EditGroup ¶
EditGroup will add or remove objects from the specified group type (e.g., "address" or "service"). Action must be add or remove. If editing a group on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) EditURLCategory ¶
EditURLCategory adds or removes URL's from the given custom URL category. Action must be add or remove If editing a URL category on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) IKEGateways ¶
IKEGateways will return a list of all configured IKE gateways on the device.
func (*PaloAlto) IPSecTunnels ¶
IPSecTunnels will return a list of all configured IPsec tunnels on the device.
func (*PaloAlto) InterfaceInfo ¶
func (p *PaloAlto) InterfaceInfo() (*InterfaceInformation, error)
InterfaceInfo will gather all of the logical and physical interface information from a firewall.
func (*PaloAlto) Jobs ¶
Jobs returns information about every job on the device. Status can be one of: all, pending, or processed. If you want information about a specific job, specify the job ID instead of one of the other options.
func (*PaloAlto) LogForwardingProfiles ¶
func (p *PaloAlto) LogForwardingProfiles() (*LogForwarding, error)
LogForwardingProfiles returns a list of all of the log forwarding profiles on the device.
func (*PaloAlto) ModifyGroupsFromCsv ¶
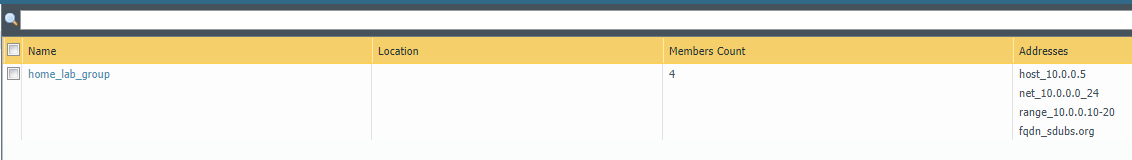
ModifyGroupsFromCsv takes a CSV file and modifies the given address or service groups with the specified action. The format of the CSV file must follow this layout:
grouptype,action,object-name,group-name,device-group
See https://github.com/scottdware/go-panos#modifying-object-groups-from-a-csv-file for complete documentation and examples.
func (*PaloAlto) Policy ¶
Policy returns information about the security policies for the given device-group. If no device-group is specified then the local rules are returned when run against a firewall. If you have pre and/or post rules, then both of them will be returned. They are separated under a Pre and Post field in the returned Policy struct. Local rules are returned in the Local field.
func (*PaloAlto) QueryLogs ¶
func (p *PaloAlto) QueryLogs(logtype string, parameters *LogParameters) (int, error)
QueryLogs allows you to pull logs from the system, given a specific log-type. Currently, the supported log types are as follows:
config, system, traffic, threat, wildfire, url, data
The LogParameters struct lists optional parameters you can use in your query. See the documentation for a full description of options. If you do not wish to use any of the optional parameters, just specify nil. The job ID is returned from the query, and should be passed to RetrieveLogs().
func (*PaloAlto) RemoveDevice ¶
RemoveDevice will remove a device from Panorama. If you specify the optional devicegroup parameter, it will only remove the device from the given device-group.
func (*PaloAlto) RemoveInterfaceFromVirtualRouter ¶
RemoveInterfaceFromVirtualRouter removes a given interface from the specified virtual-router.
func (*PaloAlto) RemoveInterfaceFromVlan ¶
RemoveInterfaceFromVlan removes a given interface from the specified vlan.
func (*PaloAlto) RemoveInterfaceFromZone ¶
RemoveInterfaceFromZone removes an interface from the specified zone.
func (*PaloAlto) RemoveTagFromObject ¶
RemoveTagFromObject will remove a single tag from an address/service object. If removing a tag on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) RemoveTagFromRule ¶
RemoveTagFromRule will remove a single tag from an rule. If removing a tag on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) RenameObject ¶
RenameObject will rename the given object from oldname to the newname. You can rename the following object types:
address, address-groups, service, service-groups, tags.
If renaming objects on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) RestartSystem ¶
RestartSystem will issue a system restart to the device.
func (*PaloAlto) RetrieveLogs ¶
RetrieveLogs will return the log data as specified in the QueryLogs() function, given the job ID. If the job status is not FIN, then you will have to query the job ID until it has finished and then it will return the results.
func (*PaloAlto) Routes ¶
func (p *PaloAlto) Routes(vr ...string) (*RoutingTable, error)
Routes will retrieve information about each route in the devices routing table(s). You can (optionally) specify a specific virtual router to retrieve routes from.
func (*PaloAlto) SecurityProfileGroups ¶
func (p *PaloAlto) SecurityProfileGroups() (*SecurityGroups, error)
SecurityProfileGroups returns a list of all of the security profile groups on the device.
func (*PaloAlto) ServiceGroups ¶
func (p *PaloAlto) ServiceGroups(devicegroup ...string) (*ServiceGroups, error)
ServiceGroups returns information about all of the service groups. You can (optionally) specify a device-group when ran against a Panorama device. If no device-group is specified, then all service groups are returned, including shared objects if ran against a Panorama device.
func (*PaloAlto) Services ¶
func (p *PaloAlto) Services(devicegroup ...string) (*ServiceObjects, error)
Services returns information about all of the service objects. You can (optionally) specify a device-group when ran against a Panorama device. If no device-group is specified, then all objects are returned, including shared objects if ran against a Panorama device.
func (*PaloAlto) SessionID ¶
SessionID will retrieve information about the given session on a firewall.
func (*PaloAlto) Sessions ¶
func (p *PaloAlto) Sessions(filter ...string) (*SessionTable, error)
Sessions will retrieve information about each session within the session table on a firewall. You can optionally define a filter, and use the same criteria as you would on the command line. The filter query must be enclosed in quotes "", and the format is:
option=value (e.g. "application=ssl")
Your filter can include multiple items, and each group must be separated by a comma, e.g.:
"application=ssl, ssl-decrypt=yes, protocol=tcp"
func (*PaloAlto) SetPanoramaServer ¶
SetPanoramaServer will configure a device to be managed by the given Panorama server's primary IP address. You can optionally add a second Panorama server by specifying an IP address for the "secondary" parameter.
func (*PaloAlto) SetShared ¶
SetShared will set Panorama's device-group to shared for all subsequent configuration changes. For example, if you set this to "true" and then create address or service objects, they will all be shared objects. Set this back to "false" to return to normal mode.
func (*PaloAlto) TagObject ¶
TagObject will apply the given tag to the specified address or service object(s). To apply multiple tags, separate them by a comma e.g.: "tag1, tag2". If you have address/service objects with the same name, then the tag(s) will be applied to all that match. If tagging objects on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) TagRule ¶
TagRule will apply the given tag to the specified rule. To apply multiple tags, separate them by a comma e.g.: "tag1, tag2". If tagging objects on a Panorama device, specify the device-group as the last parameter.
func (*PaloAlto) Tags ¶
Tags returns information about all tags on the system. You can (optionally) specify a device-group when ran against a Panorama device. If no device-group is specified, then all tags are returned, including shared objects if run against a Panorama device.
func (*PaloAlto) TemplateStacks ¶
func (p *PaloAlto) TemplateStacks() (*TemplateStacks, error)
TemplateStacks returns information about all of the template stacks in Panorama, and what templates, devices are assigned to them. This is ONLY available on Panorama version 7.0.0 and higher.
func (*PaloAlto) Templates ¶
Templates returns information about all of the templates in Panorama, and what devices they are applied to.
func (*PaloAlto) TestRouteLookup ¶
func (p *PaloAlto) TestRouteLookup(vr, destination string) (*RouteLookup, error)
TestRouteLookup will lookup the given destination IP in the virtual-router "vr" and return the results.
func (*PaloAlto) TestURL ¶
TestURL will verify what category the given URL falls under. It will return two results in a string slice ([]string). The first one is from the Base db categorization, and the second is from the Cloud db categorization. If you specify a URL with a wildcard, such as *.paloaltonetworks.com, it will not return a result.
func (*PaloAlto) URLCategory ¶
func (p *PaloAlto) URLCategory(devicegroup ...string) (*URLCategory, error)
URLCategory returns a list of all custom URL category objects. You can (optionally) specify a device-group when ran against a Panorama device. If no device-group is specified, then all objects are returned.
func (*PaloAlto) XpathClone ¶
XpathClone allows you to clone an existing part of the devices configuration. Use the xpath parameter to specify the location of the object to be cloned. Use the from parameter to specify the source object, and the newname parameter to provide a name for the cloned object.
See https://goo.gl/ZfmBB6 for details.
func (*PaloAlto) XpathConfig ¶
XpathConfig allows you to configure the device using an Xpath expression for the given xpath parameter. The element parameter can either be an XML file or an XML string when configuring the device. The action parameter can be one of:
set, edit, rename, override or delete
Set actions add, update, or merge configuration nodes, while edit actions replace configuration nodes - use the edit action with caution! If you are renaming an object, specify the new name for the object in the element parameter. If you are deleting a part of the configuration, you do not need the element parameter. For all other actions you will need to provide it.
See https://goo.gl/G1vzJT for details regarding all of the actions available.
func (*PaloAlto) XpathGetConfig ¶
XpathGetConfig allows you to view the active or candidate configuration at the location specified in the xpath parameter.
func (*PaloAlto) XpathMove ¶
XpathMove allows you to move the location of an existing configuration object. Use the xpath parameter to specify the location of the object to be moved, and the where parameter to specify type of move. You can optionally use the destination parameter to specify the destination path.
See https://goo.gl/LbkQDG for details.
func (*PaloAlto) XpathMulti ¶
XpathMulti allows you to move and clone multiple objects across device groups and virtual systems. The element parameter can be either an XML file or XML string. The action parameter must be one of: clone or move. The xpath parameter is for the destination where the addresses will be moved to. The element parameter must include in the XML the xpath for the source and the list of objects within the specified source.
See https://goo.gl/oeufnu for details.
type Policy ¶
Policy lists all of the security rules for a given device-group, or the local rules on a firewall. The IncludedRules field contains information about which rules are defined. The values are as follows:
pre, post, both, local
If both is present, then the policy contains pre and post rules.
type ProxyID ¶
type ProxyID struct {
Name string `xml:"name,attr"`
Local string `xml:"local"`
Remote string `xml:"remote"`
}
ProxyID contains information for each individual proxy-id.
type Recurrance ¶
Recurrance contains the information for external dynamic lists when it comes to how often they are downloaded. Method must be one of five-minute, hourly, daily, weekly, monthly. DayOfWeek is the name of the day, such as "tuesday." DayOfMonth is specified as a number, ranging from 1-31. Hour must be in 23-hour format, such as "03" for 3 am. The hourly and five-minute methods do not require any additional fields. DayOfWeek and DayOfMonth both require the Hour field as well.
type Route ¶
type Route struct {
VirtualRouter string `xml:"virtual-router"`
Destination string `xml:"destination"`
NextHop string `xml:"nexthop"`
Metric int `xml:"metric"`
Flags string `xml:"flags"`
Age int64 `xml:"age"`
Interface string `xml:"interface"`
}
Route contains information about each individual route in the devices routing table.
type RouteLookup ¶
type RouteLookup struct {
NextHop string
Source string
IP string
Metric int
Interface string
DataPlane string
}
RouteLookup contains the results of the operational command: test routing fib-lookup <ip> <virtual-router>.
type RoutingTable ¶
type RoutingTable struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Flags string `xml:"result>flags"`
Routes []Route `xml:"result>entry"`
}
RoutingTable contains all of the routes in the devices routing table.
type Rule ¶
type Rule struct {
Name string `xml:"name,attr"`
Tag []string `xml:"tag>member,omitempty"`
From []string `xml:"from>member,omitempty"`
To []string `xml:"to>member,omitempty"`
Source []string `xml:"source>member,omitempty"`
Destination []string `xml:"destination>member,omitempty"`
SourceUser []string `xml:"source-user>member,omitempty"`
Application []string `xml:"application>member,omitempty"`
Service []string `xml:"service>member,omitempty"`
HIPProfiles []string `xml:"hip-profiles>member,omitempty"`
Category []string `xml:"category>member,omitempty"`
Action string `xml:"action,omitempty"`
LogStart string `xml:"log-start,omitempty"`
LogEnd string `xml:"log-end,omitempty"`
LogSetting string `xml:"log-setting,omitempty"`
Disabled string `xml:"disabled,omitempty"`
URLFilteringProfile string `xml:"profile-setting>profiles>url-filtering>member,omitempty"`
FileBlockingProfile string `xml:"profile-setting>profiles>file-blocking>member,omitempty"`
AntiVirusProfile string `xml:"profile-setting>profiles>virus>member,omitempty"`
AntiSpywareProfile string `xml:"profile-setting>profiles>spyware>member,omitempty"`
VulnerabilityProfile string `xml:"profile-setting>profiles>vulnerability>member,omitempty"`
WildfireProfile string `xml:"profile-setting>profiles>wildfire-analysis>member,omitempty"`
SecurityProfileGroup string `xml:"profile-setting>group>member,omitempty"`
Description string `xml:"description,omitempty"`
}
Rule contains information about each individual security rule.
type RuleContent ¶
type RuleContent struct {
// Name of the rule.
Name string
// Tag or tags that you want the rule to be a part of.
Tag []string
// The source zone. If you wish to use "any" for the value, please use []string{"any"}.
From []string
// The destination zone. If you wish to use "any" for the value, please use []string{"any"}.
To []string
// The source address. If you wish to use "any" for the value, please use []string{"any"}.
Source []string
// The destination address. If you wish to use "any" for the value, please use []string{"any"}.
Destination []string
// The source user or users. If you wish to use "any" for the value, please use []string{"any"}.
SourceUser []string
// The applications you want to include. If you wish to use "any" for the value, please use []string{"any"}.
Application []string
// The services you want to include. If you wish to use "any" for the value, please use []string{"any"}.
Service []string
// HIP profiles to check traffic against. If you wish to use "any" for the value, please use []string{"any"}.
HIPProfiles []string
// The URL category. If you wish to use "any" for the value, please use []string{"any"}.
Category []string
// The action you want to take on the rule.
Action string
// Log at session start.
LogStart string
// Log at session end.
LogEnd string
// The log setting, such as forwarding them to Panorama.
LogSetting string
// Disable the rule.
Disabled string
// URL filtering profile.
URLFilteringProfile string
// File blocking profile.
FileBlockingProfile string
// Antivirus profile.
AntiVirusProfile string
// Anti-spyware profile.
AntiSpywareProfile string
// Vulnderability profile.
VulnerabilityProfile string
// Wildfire profile.
WildfireProfile string
// Security profile group.
SecurityProfileGroup string
// Description (optional)
Description string
}
RuleContent is used to hold the information that will be used to create a new rule
type SecurityGroups ¶
type SecurityGroups struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Profiles []SecurityProfileGroup `xml:"result>profile-group>entry"`
}
SecurityGroups contains a list of all security profile groups on the device.
type SecurityProfileGroup ¶
type SecurityProfileGroup struct {
Name string `xml:"name,attr"`
URLFiltering string `xml:"url-filtering>member"`
FileBlocking string `xml:"file-blocking>member"`
AntiVirus string `xml:"virus>member"`
AntiSpyware string `xml:"spyware>member"`
Vulnerability string `xml:"vulnerability>member"`
DataFiltering string `xml:"data-filtering>member"`
Wildfire string `xml:"wildfire-analysis>member"`
}
SecurityProfileGroup contains information about each individual security profile group.
type SecurityProfiles ¶
type SecurityProfiles struct {
URLFiltering string
FileBlocking string
AntiVirus string
AntiSpyware string
Vulnerability string
Wildfire string
Group string
}
SecurityProfiles contains a list of security profiles to apply to a rule. If you have a security group then you can just specify that and omit the individual ones.
type Serial ¶
type Serial struct {
Serial string `xml:"name,attr"`
Connected string `xml:"connected"`
UnsupportedVersion string `xml:"unsupported-version"`
Hostname string `xml:"hostname"`
IPAddress string `xml:"ip-address"`
MacAddress string `xml:"mac-addr"`
Uptime string `xml:"uptime"`
Family string `xml:"family"`
Model string `xml:"model"`
SoftwareVersion string `xml:"sw-version"`
AppVersion string `xml:"app-version"`
AntiVirusVersion string `xml:"av-version"`
WildfireVersion string `xml:"wildfire-version"`
ThreatVersion string `xml:"threat-version"`
URLDB string `xml:"url-db"`
URLFilteringVersion string `xml:"url-filtering-version"`
LogDBVersion string `xml:"logdb-version"`
VpnClientPackageVersion string `xml:"vpnclient-package-version"`
GlobalProtectClientPackageVersion string `xml:"global-protect-client-package-version"`
Domain string `xml:"domain"`
HAState string `xml:"ha>state"`
HAPeer string `xml:"ha>peer>serial"`
VpnDisableMode string `xml:"vpn-disable-mode"`
OperationalMode string `xml:"operational-mode"`
CertificateStatus string `xml:"certificate-status"`
CertificateSubjectName string `xml:"certificate-subject-name"`
CertificateExpiry string `xml:"certificate-expiry"`
ConnectedAt string `xml:"connected-at"`
CustomCertificateUsage string `xml:"custom-certificate-usage"`
MultiVsys string `xml:"multi-vsys"`
Vsys []VsysEntry `xml:"vsys>entry"`
}
Serial contains the information of each device managed by Panorama.
type Service ¶
type Service struct {
Name string `xml:"name,attr"`
TCPPort string `xml:"protocol>tcp>port,omitempty"`
UDPPort string `xml:"protocol>udp>port,omitempty"`
Description string `xml:"description,omitempty"`
Tag []string `xml:"tag>member,omitempty"`
}
Service contains information about each individual service object.
type ServiceGroup ¶
type ServiceGroup struct {
Name string `xml:"name,attr"`
Members []string `xml:"members>member,omitempty"`
Description string `xml:"description,omitempty"`
Tag []string `xml:"tag>member,omitempty"`
}
ServiceGroup contains information about each individual service group.
type ServiceGroups ¶
type ServiceGroups struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Groups []ServiceGroup `xml:"result>service-group>entry"`
}
ServiceGroups contains a slice of all service groups.
type ServiceObjects ¶
type ServiceObjects struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Services []Service `xml:"result>service>entry"`
}
ServiceObjects contains a slice of all service objects.
type Session ¶
type Session struct {
Application string `xml:"application"`
IngressInterface string `xml:"ingress"`
EgressInterface string `xml:"egress"`
VsysID int `xml:"vsys-idx"`
NATSourceAddress string `xml:"xsource"`
SourceNAT string `xml:"srcnat"`
SourcePort int `xml:"sport"`
SecurityRule string `xml:"security-rule"`
From string `xml:"from"`
Protocol int `xml:"proto"`
DestinationAddress string `xml:"dst"`
To string `xml:"to"`
State string `xml:"state"`
NATDestinationAddress string `xml:"xdst"`
NAT string `xml:"nat"`
Type string `xml:"type"`
StartTime string `xml:"start-time"`
Proxy string `xml:"proxy"`
DecryptMirror string `xml:"decrypt-mirror"`
ID int `xml:"idx"`
TotalByteCount int `xml:"total-byte-count"`
DestinationNAT string `xml:"dstnat"`
Vsys string `xml:"vsys"`
NATSourcePort int `xml:"xsport"`
NATDestinationPort int `xml:"xdport"`
Flags string `xml:"flags,omitempty"`
SourceAddress string `xml:"source"`
DestinationPort int `xml:"dport"`
}
Session holds information about each individual session on the device.
type SessionID ¶
type SessionID struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Session SingleSession `xml:"result"`
}
SessionID contains all the information regarding a specific session.
type SessionTable ¶
type SessionTable struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Sessions []Session `xml:"result>entry"`
}
SessionTable holds information about every session on the device.
type SingleSession ¶
type SingleSession struct {
ProxySession string `xml:"prxy-session"`
C2SPackets int `xml:"c2s-packets"`
FirewallEndReason string `xml:"firewall"`
ProxyStatus string `xml:"prxy-status"`
URLFilteringEnabled string `xml:"url-en"`
SYNCookies string `xml:"syncookie"`
NATRule string `xml:"nat-rule"`
QoSClass int `xml:"qos-clas"`
NATDestination string `xml:"nat-dst"`
S2CPackets int `xml:"s2c-packets"`
Slot int `xml:"slot"`
AppInsufficient string `xml:"app-insufficient"`
ProxyStarted string `xml:"prxy-started"`
CaptivePortal string `xml:"captive-portal"`
Application string `xml:"application"`
NATSource string `xml:"nat-src"`
FlowType int `xml:"flow-type"`
EndReason string `xml:"end-reason"`
Timestamp int `xml:"timestamp"`
URLCategory string `xml:"url-cat"`
SessionHASync string `xml:"sess-ha-sync"`
TunnelSession string `xml:"tunnel-session"`
HostSession string `xml:"host-session"`
C2SOctets int `xml:"c2s-octets"`
SessionEndLog string `xml:"sess-log"`
StartTime string `xml:"start-time"`
S2COctets int `xml:"s2c-octets"`
EgressInterface string `xml:"egr-if"`
NATRuleVsys string `xml:"nat-rule-vsys"`
Vsys string `xml:"vsys"`
Rule string `xml:"rule"`
SessionAger string `xml:"sess-ager"`
TimeStart int `xml:"time-start"`
Timeout int `xml:"timeout"`
QoSRule string `xml:"qos-rule"`
IngressInterface string `xml:"igr-if"`
DataplaneCPU int `xml:"cpu"`
C2SSrcUser string `xml:"c2s>src-user"`
C2SProtocol int `xml:"c2s>proto"`
C2SDestAddress string `xml:"c2s>dst"`
C2SDestUser string `xml:"c2s>dst-user"`
C2SSourceAddress string `xml:"c2s>source"`
C2SState string `xml:"c2s>state"`
C2SFrom string `xml:"c2s>source-zone"`
C2SIPVersion int `xml:"c2s>ipver"`
C2SDestPort int `xml:"c2s>dport"`
C2SSourcePort int `xml:"c2s>sport"`
C2SType string `xml:"c2s>type"`
S2CSrcUser string `xml:"s2c>src-user"`
S2CProtocol int `xml:"s2c>proto"`
S2CDestAddress string `xml:"s2c>dst"`
S2CDestUser string `xml:"s2c>dst-user"`
S2CSourceAddress string `xml:"s2c>source"`
S2CState string `xml:"s2c>state"`
S2CFrom string `xml:"s2c>source-zone"`
S2CIPVersion int `xml:"s2c>ipver"`
S2CDestPort int `xml:"s2c>dport"`
S2CSourcePort int `xml:"s2c>sport"`
S2CType string `xml:"s2c>type"`
}
SingleSession contains information about the session.
type Template ¶
type Template struct {
Name string `xml:"name,attr"`
Description string `xml:"description"`
Devices []Serial `xml:"devices>entry"`
}
Template contains information about each individual template.
type TemplateStack ¶
type TemplateStack struct {
Name string `xml:"name,attr"`
Description string `xml:"description"`
Members []string `xml:"templates>member"`
Devices []Serial `xml:"devices>entry"`
}
TemplateStack contains information about each individual template stack.
type TemplateStacks ¶
type TemplateStacks struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Templates []TemplateStack `xml:"result>template-stack>entry"`
}
TemplateStacks lists all of the template stacks in Panorama.
type Templates ¶
type Templates struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Templates []Template `xml:"result>template>entry"`
}
Templates lists all of the templates in Panorama.
type Tunnel ¶
type Tunnel struct {
Name string `xml:"name,attr"`
ProxyIDs []ProxyID `xml:"auto-key>proxy-id>entry"`
}
Tunnel contains information for each individual tunnel.
type Tunnels ¶
type Tunnels struct {
XMLName xml.Name `xml:"response"`
Status string `xml:"status,attr"`
Code string `xml:"code,attr"`
Tunnels []Tunnel `xml:"result>ipsec>entry"`
}
Tunnels contains information of all the IPsec tunnels configured on a device.